-
SolutionsSocure's versatile identity verification solutions tackle a wide spectrum of challenges, from onboarding and beyond.
-
ProductsFraud & RiskComplianceID + BiometricAccount IntelligenceExplore the future of identity verification and trust with our comprehensive suite of AI-powered products.Fraud & RiskComplianceID + BiometricAccount IntelligenceSigma Identity Fraudfor the most accurate third-party fraud detection leveraging a 360° view of digital identityPhone RiskScoreto instantly predict risk and verify phone ownershipSigma Synthetic Fraudfor uncovering complex manipulated and fabricated synthetic identity fraudAddress RiskScoreto instantly predict the risk connected with physical addressesSigma First-Party Fraudfor minimizing early payment default, bad faith dispute abuse, and chargeback lossesDigital Intelligencefor passively verifying user devices behavioral biometrics to to detect fraud and improve UXEmail RiskScoreto instantly predict risk and verify email ownershipGraph Intelligenceto quickly transform complex identity connections into actionable insightsPortfolio Scrubreveal compliance and fraud risks in your existing customer accountseCBSVfor instantly verifying a consumer-provided name-DOB-SSN match with the SSASocure Verify Plusfor precise, accurate, and inclusive identity verificationGlobal Watchlist Screening with Monitoringfor sanctions screening, PEP, and adverse media risk managementDeceased Checkfor validating deceased identities at any point in the user lifecyclePredictive DocVfor quick and accurate ID document and biometric verification with liveness detectionSocure Acccount IntelligenceVerify bank account ownership and status with inclusive, instant resultsGet customized strategies from our experts to drive your success. Start now.Get a Demo
-
Public SectorExplore public sectorSocure empowers governments to combat identity fraud while ensuring equitable access to public services. Our AI-driven platform delivers unparalleled accuracy in identity verification, helping agencies stop fraudsters without compromising access for underserved populations.
-
ResourcesExplore resourcesDive into Socure's resource center to access expert insights on identity verification and fraud prevention through eBooks, reports, articles, infographics, and our blog. Stay ahead with innovative strategies from industry leaders.
-
CompanyLearn more about usLearn more about the award-winning people and technologies that power Socure.

Best Practices for Controlling Account Takeover (ATO) with Risk Scores
As the world becomes more digital, account takeover continues to cause pain for most modern organizations, and this topic comes up regularly in Socure customer conversations. For those unfamiliar with the concept, account takeover (ATO) is an attempt to gain unauthorized account access in a digital environment using the following steps:
- Step 1: A fraudster gains access to victims’ account(s)
- Step 2: That fraudster then makes non-monetary changes to account details, like:
- A: Modifying personally identifiable information (PII)
- B: Requesting a new card
- C: Adding an authorized user
- D: Changing the password
- Step 3: From there, the fraudster carries out unauthorized transactions resulting in a financial loss, resulting in a potential loss of the victim’s customer relationship between the business and the consumer
Balancing ATO Prevention With A Seamless User Experience
Countering ATO fraud while minimizing consumer experience friction poses an ongoing challenge for financial services, fintechs, and other digital enterprises. It’s critical to stop the bad actors while not inconveniencing or frustrating good customers. This is where Risk Scores provide a valuable tool to passively control ATO while maintaining an optimal customer experience.
Enterprises usually have controls in place to mitigate ATO attacks; these include bot mitigation, behavioral biometrics, device telemetry, and transaction/event monitoring. However, as Gartner® points out, “Sophisticated fraudulent attacks can circumvent many of the legacy tools used to identify unusual activity. At the same time, the behavior of many legitimate consumers is becoming more fluid between devices and geographies and more privacy focused. This makes legacy device fingerprinting and IP address policies ineffective.” 1
Account Profile Changes: An Underutilized Control Point for Preventing ATO Fraud
Fraudsters frequently need to modify account profiles in order to execute their nefarious activities, and that means changing an account email address or phone number. Once the fraudster has redirected the account, they can take full control and make unauthorized transitions to make their illicit profit.
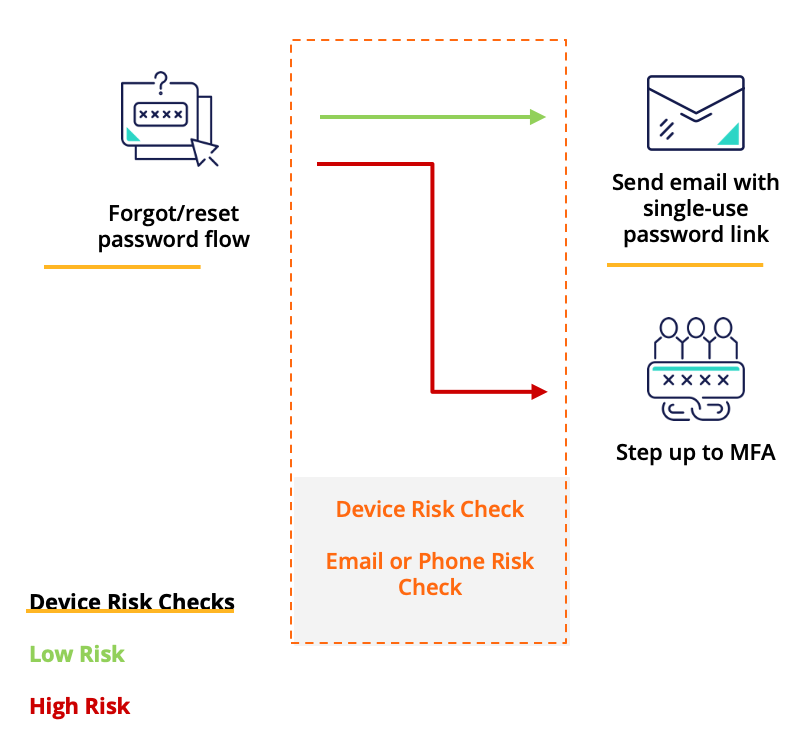
An underutilized control point is when those account profile changes are made: specifically, the modifying of an email address, phone number, or physical address on file. Before making a requested change, enterprises can validate the riskiness of that email, phone number, or address, and check the device risk level, while also checking on how closely correlated these various presented digital identity elements are with the user itself (see Figure 1).
Multichannel Risk & ATO: Added Protection for Critical Flows
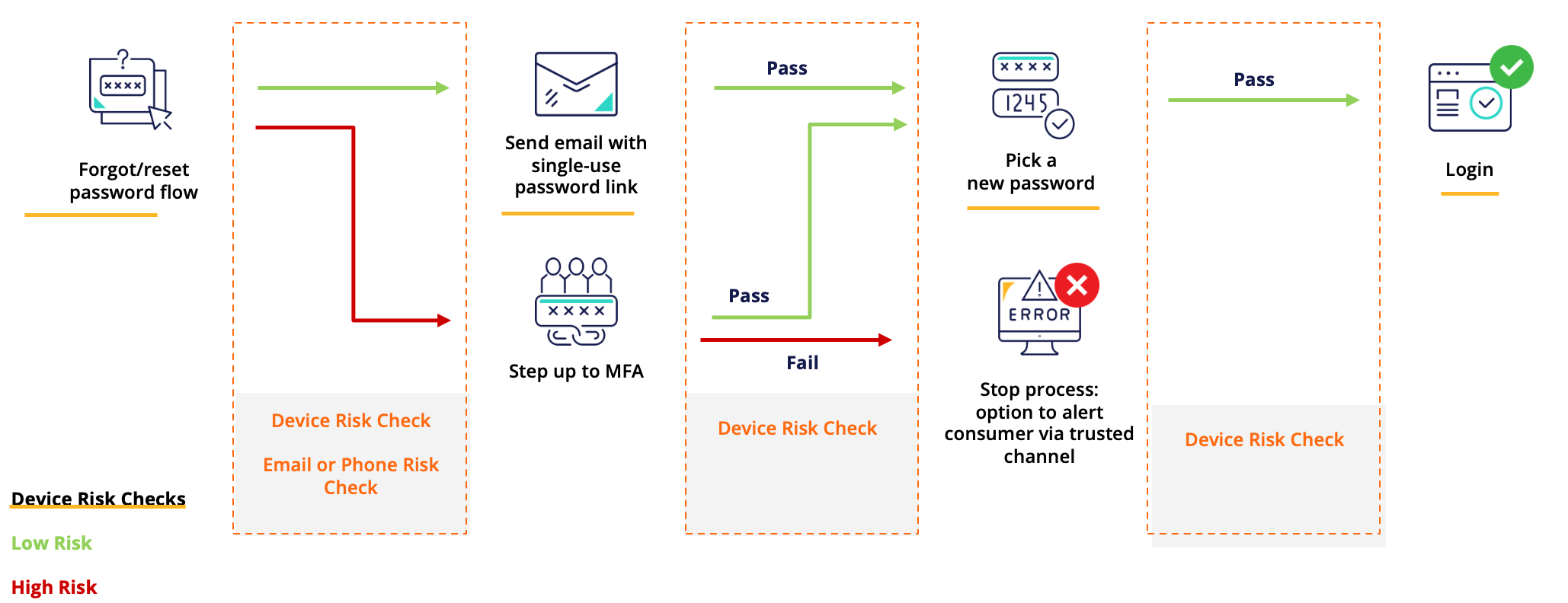
Moving beyond the profile change process, device risk can help control risk at every point of interaction on the homepage, login, and profile page for sign-ups, logins, account updates, high-value and risky transactions, and more (see below Figure 2).
Device Risk & ATO: Added Protection for Critical Process Flows
The Socure Solution
Socure’s Email RiskScore, Phone RiskScore, and Sigma Device products enable you to protect your profile change process while ensuring a smooth customer experience.
ATO is a painful and persistent problem that damages brand reputation and causes big fraud losses. To learn more about best practices in countering ATO or to speak with one of our fraud experts, please give us a shout today.
1 (“Don’t Treat Your Customer Like a Criminal”, Gartner, 1 July 2021. GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.)
Socure
Socure is the leading platform for digital identity verification and trust. Its predictive analytics platform applies artificial intelligence and machine learning techniques with trusted online/offline data intelligence from email, phone, address, IP, device, velocity, and the broader internet to verify identities in real time.